ROAAR© uses encryption to protect all data for Contractors and Employees alike. This encryption is created through the use of an SSL Certificate.
What is an SSL Certificate?
SSL Certificates are small data files that digitally bind a cryptographic key
to an organization’s details. When installed on a web server, it
activates the padlock and the https protocol and allows secure
connections from a web server to a browser. Typically, SSL
is used to secure credit card transactions, data transfer and logins,
and more recently is becoming the norm when securing browsing of social
media sites.
SSL Certificates bind together:
- A domain name, server name or hostname.
- An organizational identity (i.e. company name) and location.
An organization needs to install the SSL Certificate onto its web server to initiate a secure session with browsers. Once a secure connection is established, all web traffic between the web server and the web browser will be secure.
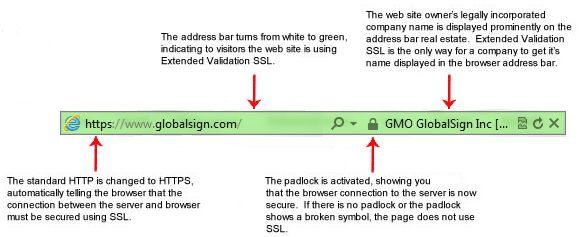
When a certificate is successfully installed on your server, the application protocol (also known as HTTP) will change to HTTPs, where the ‘S’ stands for ‘secure’. Depending on the type of certificate you purchase and what browser you are surfing the internet on, a browser will show a padlock or green bar in the browser when you visit a website that has an SSL Certificate installed.
What does a website with an SSL Certificate installed look like?
Extended Validation (EV) SSL Certificates:
How Does an SSL Certificate Work?
SSL Certificates use something called public key cryptography.
This particular kind of cryptography harnesses the power of two keys which are long strings of randomly generated numbers. One is called a private key and one is called a public key.A public key is known to your server and available in the public domain. It can be used to encrypt any message. If Alice is sending a message to Bob she will lock it with Bob’s public key but the only way it can be decrypted is to unlock it with Bob’s private key. Bob is the only one who has his private key so Bob is the only one who can use this to unlock Alice’s message. If a hacker intercepts the message before Bob unlocks it, all they will get is a cryptographic code that they cannot break, even with the power of a computer.